BYOD Implementation Examples
The following describes how you can implement the Smoothwall Filter and Firewall for using BYOD.
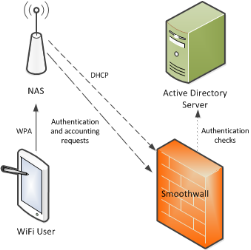
DHCP, Authentication, and Accounting Services
You can configure the Smoothwall Firewall to be the DHCP server, and the RADIUS server for both authentication, and accounting requests.
Note: To use the DHCP, you need a Unified Threat Management license.
This might be implemented as follows:
- In the network access server, the Smoothwall Firewall is configured as the RADIUS server, which receives authentication, and authorization requests
- In the network access server, the Smoothwall Firewall is also configured as the RADIUS server, which receives accounting requests
- The Smoothwall Firewall connects to an Active Directory server to perform user authentication
- The Smoothwall Firewall is the DHCP server. Therefore, it doesn't perform DHCP relays for the wireless network. The Smoothwall Firewall must be on the same subnet as the network access server for this to work.
Authentication and accounting
This implementation provides greater control over authentication services.
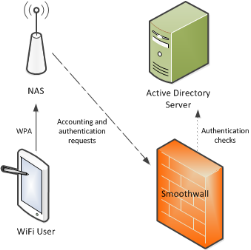
The Smoothwall Firewall will authenticate the user and authorize them to the wireless network. However, the Smoothwall Firewall is informed of the IP address assigned to the user in the RADIUS accounting packet received from the network access server. This are contained in the Framed-IP-Address attribute.
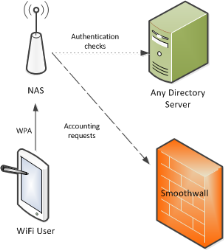
Accounting services
You can delegate user authentication and authorization to the wireless network to the network access server, and only use the Smoothwall Firewall as the RADIUS server that receives accounting requests. Typically, the Smoothwall Firewall uses the accounting requests to log the user on or off the network. For this to work the network access server must include the Framed-IP-Address attribute (and Accounting-Start or Accounting-Stop) in the RADIUS accounting packet to the Smoothwall Firewall.
This might be implemented as follows:
- The network access server can use any directory service to authenticate the user.
- In the network access server, the Smoothwall Firewall is configured as the RADIUS server that receives accounting requests.
- The network access server must send an Interim-Update at least once an hour to confirm the user’s session is still active.
- If supported, the network access server must be configured to send the users’ IP address in the Framed-IP-Address attribute of the RADIUS accounting packet, otherwise the IP address of the network access server is sent instead. This will lead to the Smoothwall Firewall being unable to log individual users on or off the wireless network.
- You can add a directory service Type of RADIUS accounting to the Smoothwall Firewall, to indicate to it that all authentication and authorization requests are provided by an external RADIUS server. You must add group mappings in the Smoothwall Firewall to map the RADIUS group, to the Smoothwall Firewall groups, see our help topic, Adding user groups.
- Optionally, to support group mappings, the network access server must be configured to send the Filter-ID RADIUS attribute in the accounting requests to the Smoothwall Firewall. The Smoothwall Firewall must also be configured to authenticate the users.
- The Smoothwall Firewall can provide DHCP services and receive RADIUS accounting requests if the network access server is configured to connect to a directory service for authentication and authorization to the wireless network.
Note: To use the DHCP services, you need a Unified Threat Management license.
Multitenant setup
You can use BYOD in a Multitenant configuration, by passing the client’s IP address into the Framed-IP-Address attribute denoting the tenant membership.
Typically, you add all network access servers’ IP addresses into the same tenant as the clients they're serving. This is essential if the network access server is unable to support sending the client’s IP address in the Framed-IP-Address attribute (the Smoothwall Firewall would receive the IP address of the network access server instead), or if Framed-IP-Address isn't sent in every accounting packet. This is to make sure that users receive the correct web filtering policies, see our help topic, Adding tenants.
Centrally managed solution
A BYOD service in a centrally managed solution, could potentially be configured with any of the implementations previously described.
You can configure the parent Smoothwall Firewall node as the primary RADIUS server, with the child nodes acting as extra RADIUS servers receiving forwarded accounting packets.
You can also configure more than one Smoothwall Firewall to act as the RADIUS server for the network access server, with each processing a different RADIUS request.
You can also configure the network access servers to use one of the Smoothwall Firewall nodes as a backup RADIUS server. However, the following limitations apply:
- The network access server must send the Framed-IP-Address attribute to all nodes, including those that aren't being used for authentication
- Each Smoothwall Firewall node must be configured to see all other Smoothwall Firewall nodes in the centrally managed solution
- You must make sure that the correct shared secret is configured for each node
- Each node must be configured to forward accounting packets to all other nodes
Note: Nodes from a centrally managed solution aren't added to the BYOD configuration automatically. You must add them separately to the Forward RADIUS accounting to section located on the BYOD page.
See our help topic, Setting up a centrally managed system.